Transform Your Business into a Cyber-Resilient Powerhouse
As cybercrime raises at an alarming rate, the imperative for stringent security measures has reached unprecedented heights. Cybercrime Magazine forecasts that the global economic impact of cybercrime is set to soar to an astronomical $10.5 trillion by 2025, underscoring the critical need for enhanced defenses in the digital age.
The rapid adoption of disruptive technologies—such as AI, social, cloud, mobile, and big data—has transformed business landscapes but also amplified the complexity of IT infrastructure and information security. This evolving digital landscape demands a proactive approach to mitigate cyber threats effectively.
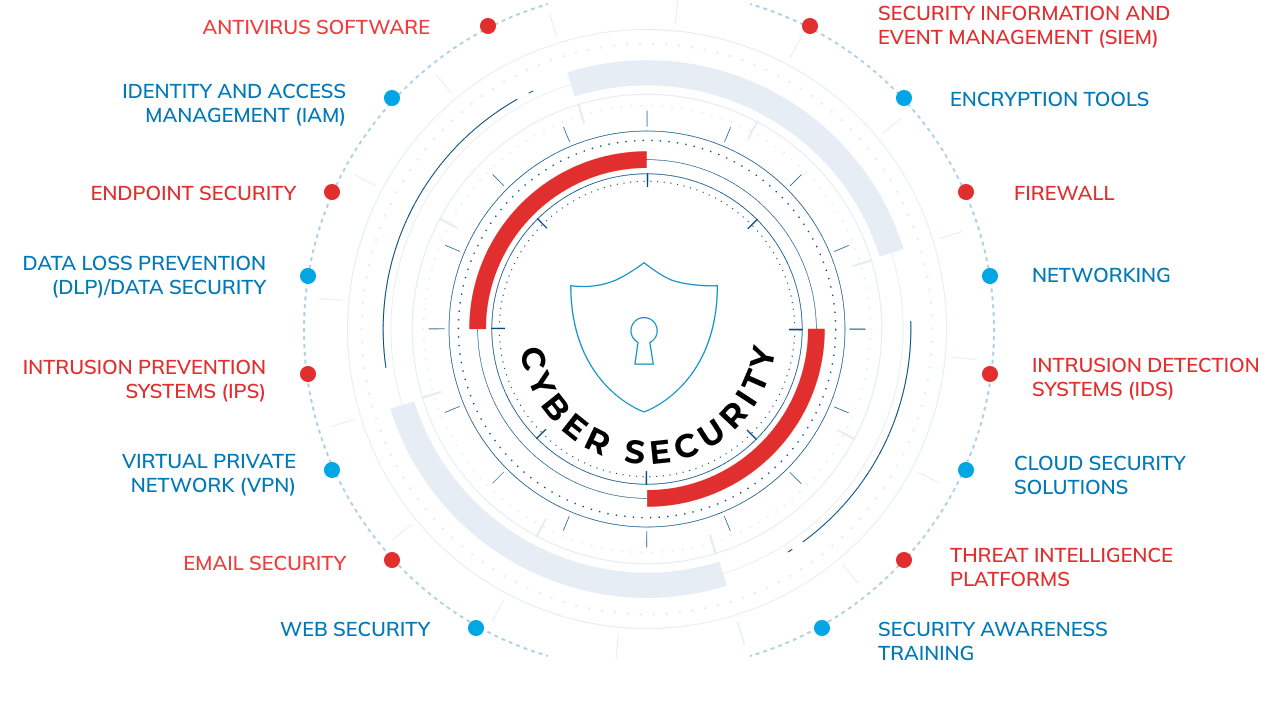
At CompQsoft, we deliver end-to-end Cyber Security Services designed to enhance the agility, flexibility, and cost-efficiency of next-generation information security and compliance programs. Our holistic, risk-driven approach encompasses Identity & Access Governance, Data Protection, Risk and Compliance, Threat Management & Mitigation, and Cybersecurity Monitoring and Management.
By partnering with CompQsoft, businesses, and government agencies can take a proactive measure against cyber threats, ensuring the safety and resilience of their mission-critical systems and digital assets. Secure your future with our comprehensive cybersecurity solutions today.